This article is a guest post by Chris Spears of Arke Systems. It was entered into The Hackies essay contest for the upcoming MarTech conference. Like it? You can register your vote in the contest by sharing it on social media, especially LinkedIn, Facebook, and Twitter.
Just like it was time for the CMO to work with the CIO, it’s time for the CMO to work with cybersecurity. It’s becoming a more pressing issue as organizations collect information.
In fact, according to research from PSFK and MasterCard, 86% of people who completed a survey said “they would invest more time or energy into adopting new payment technologies if they promised greater security.” I surmise that this ideology will only spill over into other consumer expectations surrounding security, including information collected by marketing and sales tools.
Marketing technology security isn’t just consumer facing; it’s also internal. Teams evolve — people leave, onboard, move to different departments, etc. How do you manage all the security involved with internal team members?
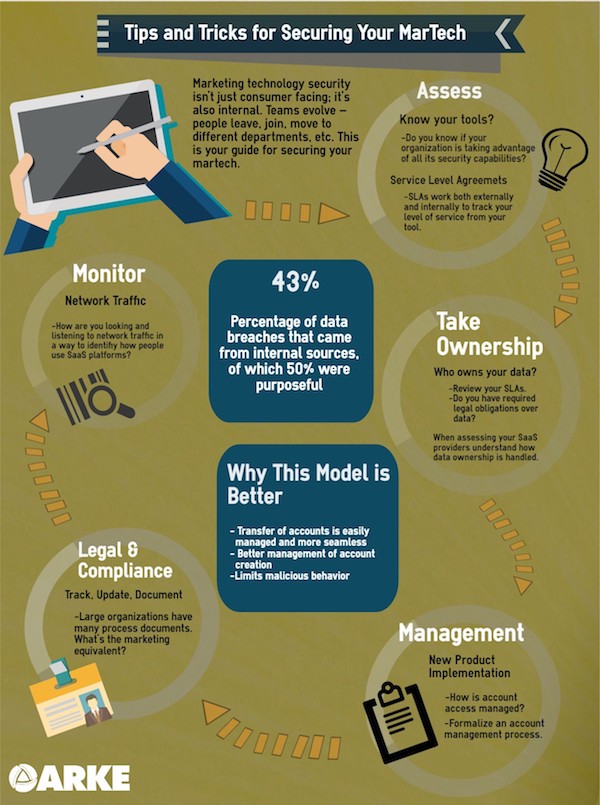
5 Tips and Tricks for Securing Your Marketing Technology
1. Assessment of SaaS Platforms. In a survey of 300 marketers who were asked how their organization planned to increase marketing agility, the majority, 43%, said they would accomplish this by implementing a marketing plan, spend management, and marketing workflow management, according to Forbes Insights on MarketingCharts.com. This plan should also include a process for assessing and implementing new technologies.
SLAs, service level agreements, work both externally and internally to track your level of service from a tool. You or someone in your organization needs to understand what you should be receiving from your service. An SLA describes who owns what, where responsibilities lie, and level of support. It exists to ensure you’re receiving the agreed upon service level from the tool; make sure you’re receiving all it defines.
In particular, do you know if your organization is taking advantage of all a SaaS platform’s security capabilities? For example, Salesforce allows customers to whitelist IP addresses. This means that an admin can set up the system to only allow IP addresses in a certain range to connect.
2. Ownership. This one is big. Do you know who owns your data? Many organizations don’t. It’s a large concern for enterprise organizations, especially when dealing with consumer data,but smaller organizations should be concerned as well.
When assessing your SaaS providers, understand how data ownership is handled. Ownership implies control over the information. Are you sure you’re the one in control?
Determining ownership of your data should also be process oriented. It may not make a difference if the information isn’t personally identifiable. Determine your criteria for when it does make a difference.
3. Governance/Process Management. When most organizations stand up new products, they do so under an employee account, which doesn’t necessarily seem like an issue at first. If the account is tied to the individual’s company account it shouldn’t matter, right? Wrong.
What happens when this individual is on vacation or no longer with the company and someone needs admin access? There’s a better way to manage accounts. 43% of data breaches came from internal sources, per an Intel report, and 50% of those breaches were purposeful. From the time you onboard a new employee to the point where they leave, there are chances for missteps when it comes to data. Do you have a formal process for tracking who has access and authorization levels to what?
The only time I suggest a team share a password or account is when it’s unnecessary or impossible to have multiple accounts tied to a tool. For example, YouTube is used heavily for company video content but it’s tied to a singular company Google email account. Not everyone on your team will be uploading or editing content but may need access to edit or retrieve information. This is where it becomes important to maintain security with regular password changes.
Formalize a process for managing accounts through one master account. A technique we use is tying all products to one email account shared by the marketing team. The same can be applied with other teams. There should also be a process for when someone leaves the team. Passwords should change periodically to maintain internal security. On an external level determine how long someone should stay in your database. When does someone need to be asked if they still want to be part of your mailing list or how long should they have access to an inactive account?
4. Legal and Compliance. Large organizations have many process documents. What is marketing’s equivalent? This is different form my third point on governance and process management. This is focused on how to track, update, and document those processes.
According to a report by IS Discussions, “52% percent of employees see no security risk to their employer in sharing work logins.” Security risks exist with personal logins when information is personally identifiable or it puts the company at jeopardy when sharing occurs between departments unnecessarily.
For example, IT has specific permissions and authorization levels that shouldn’t be shared with different departments. Marketing has access to social media accounts that publicly represent the company and those passwords shouldn’t be shared with other departments. This makes onboarding new employees and overall processes much easier. If someone needs access to something there should be documentation for how they obtain it.
5. Network Traffic. How are you looking and listening to network traffic in a way to identify how people use SaaS platforms? 80% of organizations believe detecting possibly compromised credentials is important. At a more technical level, organizations can see how employees are using a platform. If multiple parties try logging into the same account with a singular password it should tell you a lot about access and how it’s being used.
IT is at the forefront of monitoring network traffic. Network monitoring is the use of a tool or software platform to scan the network ensuring there are no issues to report back to your system administrator. It’s a technical watchdog. There are free and paid tools and software packages available. Your best bet is to work with IT and have them alert you to any suspicious behavior relating to your marketing stack.
How This Model Works
To summarize this hack, there are five simple things you can do to secure your marketing technologies.
- Assess all your platforms and know the level of service you should be receiving.
- Know who owns what. Before diving head-first into using a system understand how data ownership works for the tool.
- Have internal processes for managing access to tools. It makes a world of difference in how you’ll be able to transition access and roles.
- Document your processes and keep them up to date. New employees should easily be able to pick up on how they’ll receive access to the tools they need, how access is managed, and who they reach out to for troubleshooting.
- Monitor your network traffic to understand how people are using your SaaS platforms.
Happy hacking!
What did you think of this article as an entry in The Hackies essay contest for the upcoming MarTech conference? If you liked it, you can register your vote in the contest by sharing it on LinkedIn, Facebook, and Twitter.
Have a marketing/technology/management “hack” that you want to share with the world? Consider entering The Hackies yourself — we’d love to learn from your experience and insight!